How To Change Your Nat Type To Open
Contents
Introduction
This document explains configuring Network Address Translation (NAT) on a Cisco router for use in common network scenarios. The target audition of this document is kickoff time NAT users.
Note:In this document, when the net, or an cyberspace device is referred to, it means a device on whatsoever external network.
Prerequisites
Requirements
This document requires a basic knowledge of the terms used in connection with NAT. Some of the definitions can be found in NAT: Local and Global Definitions.
Components Used
The information in this document is based on these software and hardware versions:
-
Cisco 2500 Series Routers
-
Cisco IOS® Software Release 12.2 (10b)
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that yous understand the potential bear upon of any control.
Conventions
Refer to Cisco Technical Tips Conventions for more information on document conventions.
Quick Beginning Steps for Configuring and Deploying NAT
When you configure NAT, information technology is sometimes difficult to know where to brainstorm, particularly if you are new to NAT. These steps guide y'all to define what you desire NAT to exercise and how to configure it:
-
Define NAT inside and exterior interfaces.
-
Do users be off multiple interfaces?
-
Are there multiple interfaces going to the internet?
-
-
Define what y'all're trying to accomplish with NAT.
-
Are you lot trying to allow internal users to access the cyberspace?
-
Are you trying to allow the internet to access internal devices (such as a mail service server or web server)?
-
Are you trying to redirect TCP traffic to another TCP port or address?
-
Are you lot using NAT during a network transition (for example, you changed a server'south IP address and until you tin update all the clients you want the not-updated clients to be able to access the server using the original IP address as well every bit allow the updated clients to admission the server using the new address)?
-
Are y'all using NAT to allow overlapping networks to communicate?
-
-
Configure NAT in order to reach what you lot defined above. Based on what you defined in step 2, you demand make up one's mind which of the following features to use:
-
Static NAT
-
Dynamic NAT
-
Overloading
-
Any combination of the higher up
-
-
Verify the NAT performance.
Each of these NAT examples guides yous through steps i through 3 of the Quick Start Steps higher up. These examples describe some common scenarios in which Cisco recommends you deploy NAT.
Defining NAT Inside and Outside Interfaces
The first step to deploy NAT is to ascertain NAT within and outside interfaces. You may find it easiest to define your internal network as inside, and the external network every bit outside. However, the terms internal and external are subject to arbitration besides. This figure shows an case of this.
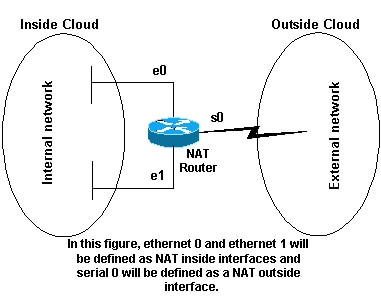
Instance: Allowing Internal Users to Access the Internet
You may want to let internal users to access the internet, but you may not have enough valid addresses to adjust everyone. If all communication with devices in the internet originate from the internal devices, you need a single valid accost or a pool of valid addresses.
This figure shows a simple network diagram with the router interfaces defined as inside and outside:
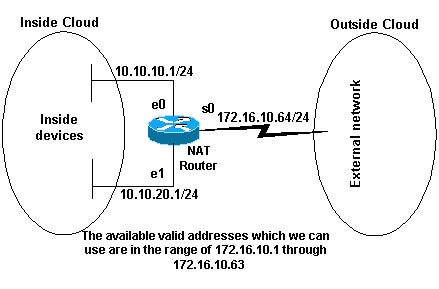
In this example, you want NAT to permit certain devices (the offset 31 from each subnet) on the within to originate communication with devices on the outside by translating their invalid address to a valid accost or pool of addresses. The pool has been defined as the range of addresses 172.16.x.1 through 172.16.10.63.
Now you are fix to configure NAT. In social club to accomplish what is defined above, apply dynamic NAT. With dynamic NAT, the translation table in the router is initially empty and gets populated once traffic that needs to be translated passes through the router. Equally opposed to static NAT, where a translation is statically configured and is placed in the translation table without the need for whatever traffic.
In this example, you tin configure NAT to translate each of the inside devices to a unique valid address, or to translate each of the inside devices to the same valid accost. This second method is known as overloading. An instance of how to configure each method is given here.
Configuring NAT to Permit Internal Users to Admission the Internet
| NAT Router |
|---|
interface ethernet 0 ip address 10.x.10.1 255.255.255.0 ip nat inside !--- Defines Ethernet 0 with an IP address and equally a NAT within interface. interface ethernet i ip address 10.10.20.i 255.255.255.0 ip nat within !--- Defines Ethernet i with an IP address and equally a NAT inside interface. interface serial 0 ip address 172.16.10.64 255.255.255.0 ip nat outside !--- Defines serial 0 with an IP address and equally a NAT exterior interface. ip nat pool no-overload 172.sixteen.ten.i 172.16.x.63 prefix 24 ! !--- Defines a NAT pool named no-overload with a range of addresses !--- 172.16.10.1 - 172.16.ten.63. ip nat inside source list 7 pool no-overload ! ! !--- Indicates that whatever packets received on the inside interface that !--- are permitted by access-list vii has !--- the source accost translated to an address out of the !--- NAT pool "no-overload". access-list vii allow ten.x.10.0 0.0.0.31 access-list 7 permit ten.10.twenty.0 0.0.0.31 !--- Access-listing vii permits packets with source addresses ranging from !--- ten.10.10.0 through x.10.10.31 and x.ten.20.0 through x.10.xx.31. |
Note:Cisco highly recommends that you do not configure access lists referenced past NAT commands with permit any. Using let any tin upshot in NAT consuming too many router resource which tin cause network issues.
Notice in the previous configuration that only the first 32 addresses from subnet 10.10.10.0 and the starting time 32 addresses from subnet ten.10.20.0 are permitted by access-list 7. Therefore, only these source addresses are translated. There may be other devices with other addresses on the inside network, merely these are non translated.
The final footstep is to verify that NAT is operating as intended.
Configuring NAT to Allow Internal Users to Access the Net Using Overloading
| NAT Router |
|---|
interface ethernet 0 ip address 10.ten.10.1 255.255.255.0 ip nat within !--- Defines Ethernet 0 with an IP accost and equally a NAT inside interface. interface ethernet one ip address 10.ten.xx.one 255.255.255.0 ip nat inside !--- Defines Ethernet 1 with an IP address and equally a NAT inside interface. interface serial 0 ip address 172.xvi.10.64 255.255.255.0 ip nat exterior !--- Defines serial 0 with an IP address and equally a NAT outside interface. ip nat pool ovrld 172.sixteen.10.one 172.xvi.ten.i prefix 24 ! !--- Defines a NAT puddle named ovrld with a range of a unmarried IP !--- address, 172.xvi.10.i. ip nat within source list vii pool ovrld overload ! ! ! ! !--- Indicates that any packets received on the inside interface that !--- are permitted by access-list vii has the source accost !--- translated to an address out of the NAT pool named ovrld. !--- Translations are overloaded, which allows multiple inside !--- devices to be translated to the same valid IP address. access-list 7 permit 10.10.ten.0 0.0.0.31 access-list vii let ten.10.twenty.0 0.0.0.31 !--- Access-list seven permits packets with source addresses ranging from !--- ten.10.10.0 through 10.10.ten.31 and ten.10.20.0 through x.ten.20.31. |
Note in the previous second configuration, the NAT pool "ovrld"merely has a range of i address. The keyword overload used in the ip nat inside source list vii puddle ovrld overload command allows NAT to translate multiple within devices to the unmarried address in the puddle.
Another variation of this command is ip nat within source list vii interface serial 0 overload, which configures NAT to overload on the address that is assigned to the serial 0 interface.
When overloading is configured, the router maintains enough information from higher-level protocols (for case, TCP or UDP port numbers) to translate the global address dorsum to the right local accost. For definitions of global and local address, refer to NAT: Global and Local Definitions.
The last step is to verify that NAT is operating as intended.
Example: Allowing the Cyberspace to Access Internal Devices
Yous may need internal devices to exchange information with devices on the internet, where the communication is initiated from the internet devices, for example, email. It is typical for devices on the internet to transport email to a post server that resides on the internal network.
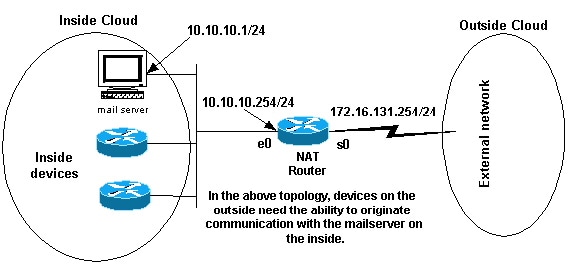
Configuring NAT to Allow the Internet to Access Internal Devices
In this example, you offset define the NAT inside and outside interfaces, every bit shown in the previous network diagram.
Second, you define that you want users on the inside to be able to originate communication with the outside. Devices on the outside should be able to originate advice with only the mail server on the within.
The third step is to configure NAT. To achieve what you have defined, you can configure static and dynamic NAT together. For more information on how to configure this example, refer to Configuring Static and Dynamic NAT Simultaneously.
The final step is to verify that NAT is operating equally intended.
Case: Redirecting TCP Traffic to Another TCP Port or Address
Having a web server on the internal network is another example of when it may be necessary for devices on the net to initiate communication with internal devices. In some cases the internal web server may be configured to listen for spider web traffic on a TCP port other than port eighty. For example, the internal web server may exist configured to mind to TCP port 8080. In this case, you tin use NAT to redirect traffic destined to TCP port lxxx to TCP port 8080.
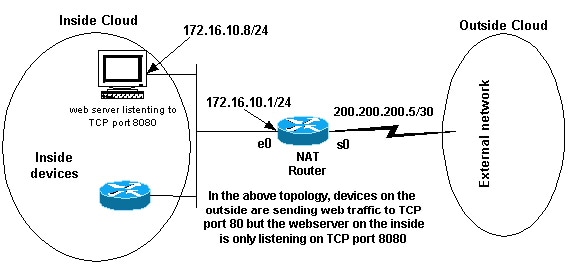
Afterwards yous define the interfaces as shown in the previous network diagram, you may decide that you want NAT to redirect packets from the exterior destined for 172.16.10.viii:80 to 172.16.ten.8:8080. Y'all tin can utilise a static nat control in order to interpret the TCP port number to achieve this. A sample configuration is shown here.
Configuring NAT to Redirect TCP Traffic to Another TCP Port or Accost
| NAT Router |
|---|
interface ethernet 0 ip accost 172.16.10.ane 255.255.255.0 ip nat inside !--- Defines Ethernet 0 with an IP address and every bit a NAT inside interface. interface series 0 ip accost 200.200.200.5 255.255.255.252 ip nat outside !--- Defines series 0 with an IP address and every bit a NAT outside interface. ip nat within source static tcp 172.xvi.10.8 8080 172.xvi.x.8 fourscore !--- Static NAT command that states whatever bundle received in the inside !--- interface with a source IP accost of 172.xvi.10.8:8080 is !--- translated to 172.16.10.eight:80. |
Note that the configuration clarification for the static NAT control indicates whatsoever packet received in the inside interface with a source address of 172.xvi.10.8:8080 is translated to 172.16.10.8:80. This likewise implies that whatsoever packet received on the exterior interface with a destination address of 172.16.10.viii:80 has the destination translated to 172.16.x.8:8080.
The concluding step is to verify that NAT is operating equally intended.
evidence ip nat translations Pro Inside global Inside local Exterior local Outside global tcp 172.16.10.8:lxxx 172.sixteen.x.eight:8080 --- ---
Example: Using NAT During a Network Transition
Deploying NAT is useful when you need to readdress devices on the network or when yous supervene upon i device with another. For instance, if all devices in the network use a particular server and this server needs to be replaced with a new one that has a new IP address, the reconfiguration of all the network devices to use the new server address takes some time. In the concurrently, you lot tin employ NAT in order to configure the devices with the former address to translate their packets to communicate with the new server.
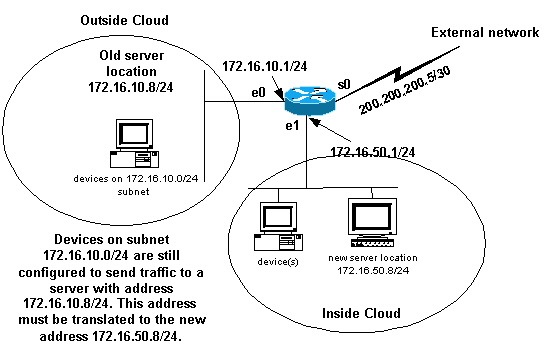
Once you have divers the NAT interfaces as shown higher up, y'all may decide that you desire NAT to allow packets from the outside destined for the old server address (172.sixteen.10.viii) to be translated and sent to the new server address. Note that the new server is on another LAN, and devices on this LAN or any devices reachable through this LAN (devices on the inside office of the network), should be configured to apply the new server'south IP address if possible.
You lot can use static NAT to accomplish what y'all need. This is a sample configuration.
Configuring NAT for Employ During a Network Transition
| NAT Router |
|---|
interface ethernet 0 ip address 172.xvi.x.ane 255.255.255.0 ip nat outside !--- Defines Ethernet 0 with an IP address and as a NAT outside interface. interface ethernet 1 ip address 172.16.50.1 255.255.255.0 ip nat inside !--- Defines Ethernet ane with an IP address and equally a NAT inside interface. interface serial 0 ip address 200.200.200.five 255.255.255.252 !--- Defines serial 0 with an IP accost. This interface is not !--- participating in NAT. ip nat inside source static 172.16.fifty.8 172.16.x.8 !--- States that any packet received on the inside interface with a !--- source IP address of 172.16.l.eight is translated to 172.16.10.8. |
Annotation that the within source NAT command in this example also implies that packets received on the exterior interface with a destination address of 172.16.10.8 has the destination address translated to 172.sixteen.50.viii.
The terminal step is to verify that NAT is operating as intended.
Case: Using NAT in Overlapping Networks
Overlapping networks effect when you assign IP addresses to internal devices that are already existence used by other devices within the cyberspace. Overlapping networks likewise result when two companies, both of whom use RFC 1918 ![]() IP addresses in their networks, merge. These two networks need to communicate, preferably without having to readdress all their devices. Refer to Using NAT in Overlapping Networks for more information on the configuration of NAT for this purpose.
IP addresses in their networks, merge. These two networks need to communicate, preferably without having to readdress all their devices. Refer to Using NAT in Overlapping Networks for more information on the configuration of NAT for this purpose.
Difference between 1-to-1 Mapping and Many-to-Many
A static NAT configuration creates a one-to-one mapping and translates a specific address to another address. This blazon of configuration creates a permanent entry in the NAT table every bit long as the configuration is nowadays and enables both within and outside hosts to initiate a connection. This is by and large useful for hosts that provide awarding services like mail, spider web, FTP and so forth. For example:
Router(config)#ip nat inside source static 10.3.2.11 10.41.10.12 Router(config)#ip nat within source static 10.three.2.12 ten.41.10.thirteen
Dynamic NAT is useful when fewer addresses are available than the actual number of hosts to be translated. It creates an entry in the NAT table when the host initiates a connection and establishes a one-to-one mapping between the addresses. But, the mapping tin vary and information technology depends upon the registered address bachelor in the pool at the time of the communication. Dynamic NAT allows sessions to be initiated only from inside or outside networks for which it is configured. Dynamic NAT entries are removed from the translation table if the host does not communicate for a specific period of time which is configurable. The address is then returned to the pool for use by another host.
For example, complete these steps of the detailed configuration:
-
Create a pool of addresses
Router(config)#ip nat pool MYPOOLEXAMPLE 10.41.10.1 10.41.10.41 netmask 255.255.255.0
-
Create an access-list for the inside networks that has to exist mapped
Router(config)#admission-list 100 permit ip 10.3.2.0 0.0.0.255 any
-
Acquaintance the admission-list 100 that is selecting the internal network 10.three.2.0 0.0.0.255 to be natted to the puddle MYPOOLEXAMPLE and then overload the addresses.
Router(config)#ip nat inside source listing 100 pool MYPOOLEXAMPLE overload
Verifying NAT Functioning
Once you've configured NAT, verify that it is operating equally expected. You can practice this in a number of ways: using a network analyzer, show commands, or debug commands. For a detailed example of NAT verification, refer to Verifying NAT Performance and Basic NAT Troubleshooting.
Conclusion
The examples in this document demonstrate quick start steps can assist y'all configure and deploy NAT. These quick first steps include:
-
Defining NAT inside and outside interfaces.
-
Defining what you are trying to accomplish with NAT.
-
Configuring NAT in order to accomplish what you defined in Footstep 2.
-
Verifying the NAT operation.
In each of the previous examples, various forms of the ip nat inside command were used. Yous can also apply the ip nat outside control in order to accomplish the same objectives, but keep in mind the NAT guild of operations. For configuration examples that use the ip nat outside commands, refer to Sample Configuration Using the ip nat outside source listing Command and Sample Configuration Using the ip nat outside source static Control.
The previous examples also demonstrated these deportment:
| Control | Action |
|---|---|
| ip nat within source |
|
| ip nat outside source |
|
Related Information
- NAT Support Page
- IP Routed Protocols Support Page
- IP Routing Support Page
- How NAT Works
- NAT Order of Operation
- Frequently Asked Questions nigh Cisco IOS NAT
- Technical Support & Documentation - Cisco Systems
Revision History
| Revision | Publish Engagement | Comments |
|---|---|---|
| ane.0 | 02-May-2014 | Initial Release |
Source: https://www.cisco.com/c/en/us/support/docs/ip/network-address-translation-nat/13772-12.html
Posted by: jamesfarinell1998.blogspot.com


0 Response to "How To Change Your Nat Type To Open"
Post a Comment